-
-
[原创]联通光猫管理员密码分析,不安全的密码方案
-
发表于:
2020-5-24 22:59
15963
-
联通光猫型号:HG220GS-U
软件版本:E00L3.03
运营商一直在做光猫防破解,对抗升级还是比较快的,所有的分析结论都和版本绑定的,因为运营商或者路由器的开发商看到后可能立马就改了。
我自己主要是要改为桥接,这个需求其实打联通的报修电话让局端改一下应该就能搞定。不过几年之前看过一两个老版本的教程,也照葫芦画瓢破解成功了,但我手上的这个版本有点麻烦,现有的教程基本都失效了。有点好奇,这次花点时间仔细看了一下,不过这次被某些人打击得比较厉害,说果然是IT狗云云,只知道和代码过不去。都云作者痴,谁解其中味!
这个光猫,先要用普通的user用户和印在光猫背面的密码登录进去,然后改链接为7d1K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4i4K6u0r3M7$3g2J5N6X3#2F1k6%4u0Q4x3X3g2Z5N6r3#2D9i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4K6W2o6i4@1p5^5i4@1f1^5i4@1u0r3i4K6V1&6i4@1f1@1i4@1t1^5i4@1q4m8i4@1f1&6i4@1p5I4i4@1t1#2i4@1f1&6i4K6W2p5i4@1p5J5i4@1f1@1i4@1t1^5i4@1q4p5i4@1f1$3i4K6S2m8i4K6S2m8i4@1f1%4i4@1q4q4i4@1p5I4i4@1f1%4i4K6V1H3i4K6R3$3i4@1f1#2i4K6V1I4i4K6V1^5i4@1f1#2i4@1t1^5i4K6V1H3i4@1f1#2i4K6S2r3i4@1t1%4k6h3&6S2j5X3I4W2i4@1g2r3i4@1u0o6i4K6S2o6N6r3g2D9L8X3g2@1i4@1f1K6i4K6R3H3i4K6R3I4k6Y4c8H3i4@1f1$3i4K6W2o6i4K6S2p5i4@1f1#2i4K6S2m8i4@1p5I4i4@1f1@1i4@1t1&6i4K6W2r3k6h3&6S2j5X3I4W2i4@1f1@1i4@1u0m8i4K6R3$3i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1$3i4@1t1K6i4@1p5^5i4@1f1$3i4K6R3@1i4K6S2r3i4@1f1#2i4K6S2r3i4@1q4m8i4@1f1&6i4K6V1J5i4K6R3^5i4@1f1#2i4@1q4r3i4@1t1&6e0p5q4z5i4@1f1@1i4@1t1^5i4K6R3H3i4@1f1@1i4@1u0q4i4@1p5%4i4@1f1#2i4@1u0o6i4K6R3H3i4@1f1$3i4K6V1@1i4@1u0q4i4@1f1^5i4@1q4q4i4@1u0r3i4@1f1&6i4K6V1%4i4@1q4q4i4@1f1K6i4K6R3H3i4K6R3J5N6r3g2D9L8X3g2@1i4@1f1$3i4K6W2o6i4K6S2p5i4@1f1#2i4K6S2m8i4@1p5I4i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1&6i4@1u0n7i4K6V1^5i4@1f1^5i4@1q4q4i4@1p5@1i4@1f1%4i4K6V1@1i4@1p5^5i4@1f1$3i4K6R3^5i4@1t1%4i4@1f1#2i4K6V1H3i4K6S2p5i4@1f1#2i4K6V1J5i4K6S2o6i4@1f1#2i4@1q4r3i4K6R3$3i4@1f1%4i4@1p5H3i4K6R3I4i4@1f1&6i4K6R3K6i4@1u0p5i4@1f1$3i4K6V1^5i4@1q4r3j5h3c8E0K9h3&6Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8e0g2Q4z5o6g2Q4b7e0g2@1k6h3I4F1k6i4c8Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8e0S2Q4b7V1k6Q4z5e0m8Q4c8e0S2Q4b7e0q4Q4z5p5y4K6K9q4!0q4y4g2!0n7x3q4!0n7x3g2!0q4y4W2)9&6z5q4!0m8c8W2!0q4y4W2)9&6z5g2!0m8c8g2!0q4z5g2)9^5x3q4)9&6b7g2!0q4y4#2)9&6b7g2)9^5y4s2y4Z5k6h3I4D9i4@1f1%4i4K6V1#2i4K6S2o6i4@1f1&6i4K6W2p5i4@1p5J5i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1^5i4@1u0r3i4K6V1&6i4@1f1@1i4@1u0m8i4K6W2n7i4@1f1$3i4K6V1^5i4@1q4r3i4@1f1#2i4K6W2o6i4@1p5^5i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1@1i4@1t1^5i4K6S2m8i4@1f1@1i4@1u0n7i4K6V1@1i4@1f1%4i4@1u0n7i4K6R3$3i4@1f1$3i4K6V1H3i4K6W2o6i4@1f1^5i4K6R3K6i4@1u0p5i4@1f1$3i4K6V1H3i4K6W2o6i4@1f1#2i4K6R3^5i4@1t1H3i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1K6i4K6R3H3i4K6R3J5
既然telnet、ftp权限都有了,那就把文件拿出来分析好了。最后要分析的是下面三个文件,关键函数是cgiAuthAdminPassword(),点到为止,有兴趣的可以自己看看。话说Ghidra对MIPS的反编译还是可以看的。新版的IDA 7.5虽然支持MIPS反编译,不过我没有。
/bin/httpd
/lib/public/libcms_util.so
/lib/public/libaes.so
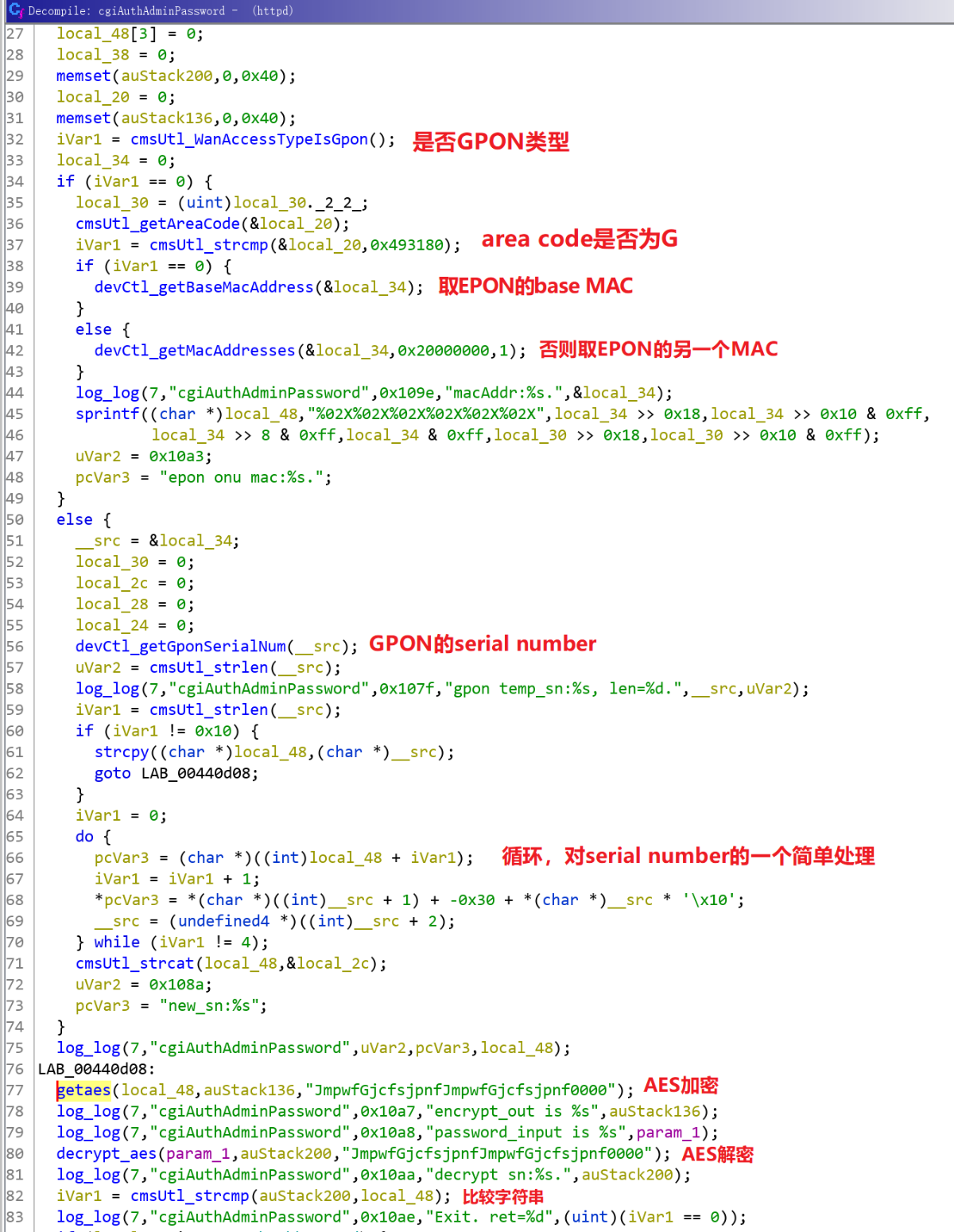
下面是根据光猫MAC地址计算CUAdmin这个用户的密码。EPON的猫需要用其base MAC,也就是“设备基本信息”那个页面中看到的MAC/SN的值,大写。可以看出这个计算很简单,就是用零补齐后AES加密。EPON类型的光猫,这个密码和area code也有关。GPON类型的光猫,则是用其serial number计算的,此处未体现。所以光猫的WEB端口千万不要针对WAN一侧开放,否则被探测出MAC地址的话,有可能随便被人访问。LAN侧如果是很多人能访问的光猫,也得小心。本质上光猫的这个管理员密码设定是不安全的,虽然是一机一码,然而却是确定的,重复一次:这个密码方案是不安全的!
所幸的是,管理员CUAdmin账户默认没开启,需要用一机一码的user帐号登录进去后才能开启。至于user帐号的密码,有待分析。
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
最后于 2020-5-25 17:59
被blowfish编辑
,原因: