老套路扫一下目录

貌似只有君子协定有用,打开看看
打开1ndexx.php 发现打不开,
尝试一下是否有备份
发现了一串代码:
构造payload:
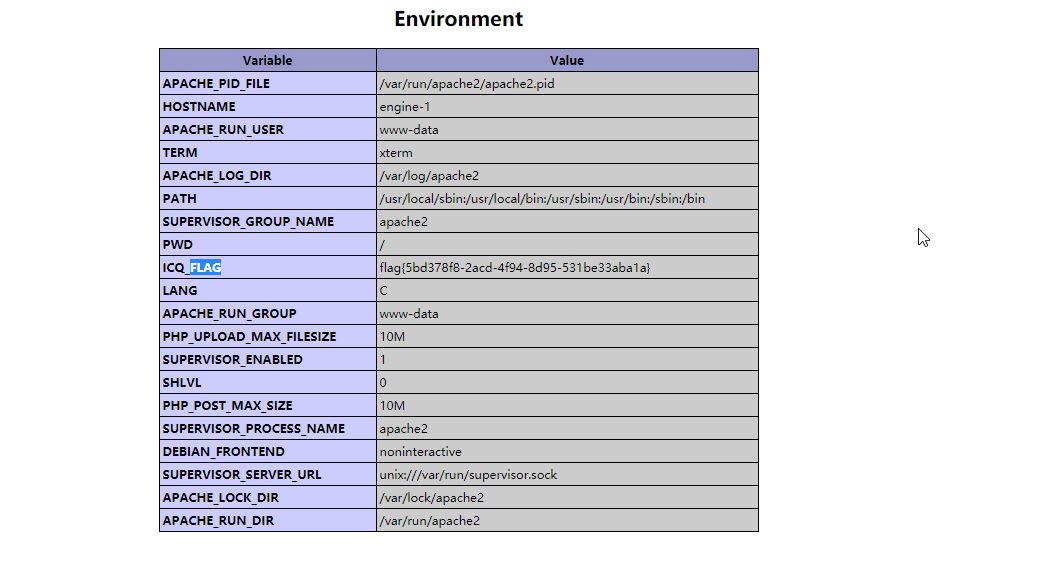
然后访问一下hack.php查看phpinfo
本来只是想指向探针看一下,没想到flag直接给了
打开发现是yii2反序列化
随即打开百度,来找一下复现:
253K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0M7q4)9J5k6i4N6W2K9i4S2A6L8W2)9J5k6i4q4I4i4K6u0W2j5$3!0E0i4K6u0r3M7#2)9K6c8W2)9#2k6W2)9#2k6X3u0A6P5W2)9K6c8p5#2*7g2e0g2y4c8p5V1H3e0@1c8u0y4f1#2c8i4K6y4p5i4K6y4p5i4K6t1$3j5h3#2H3i4K6y4n7L8h3W2V1i4K6y4p5x3U0t1@1y4K6b7^5y4e0p5J5z5g2)9J5y4X3q4E0M7q4)9K6b7X3W2V1P5q4)9K6c8o6q4Q4x3U0k6S2L8i4m8Q4x3@1u0K6L8W2)9K6c8r3t1J5y4$3f1K6k6X3f1^5y4o6g2V1j5h3g2W2x3X3k6T1x3e0y4T1j5U0W2X3x3K6k6X3y4e0y4S2j5U0b7H3
然后回到题目,按照常理我扫了一下网站目录,发现了www.zip" :

下载到本地发现正好是源码,就在本地搭建环境
丢进去phpstudy里,按照大佬的漏洞复现,在controllers下创建Controller.php
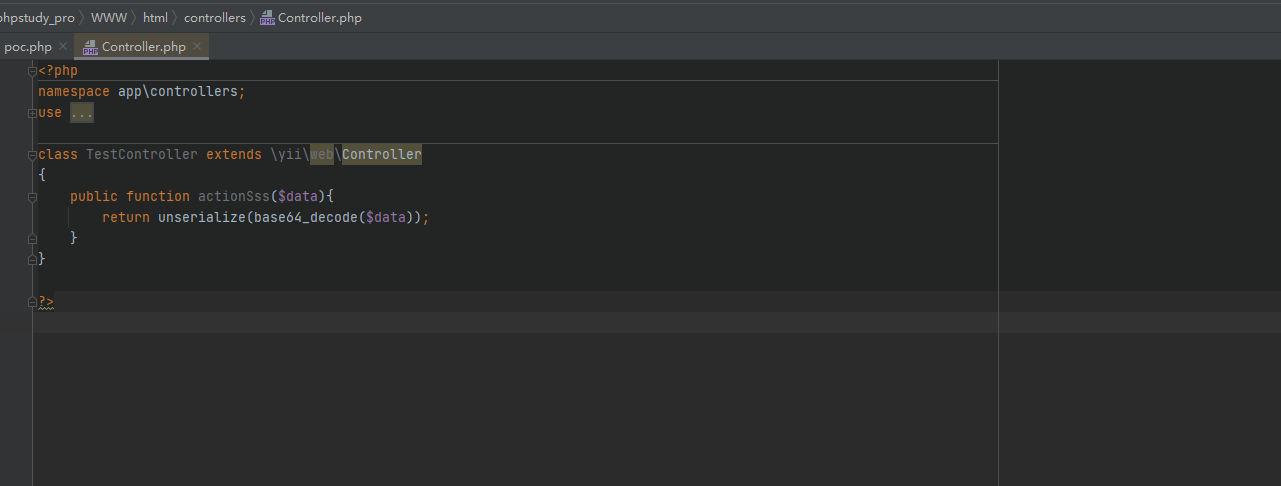
然后再新建个poc.php
在里面写:
然后再生成一下payload
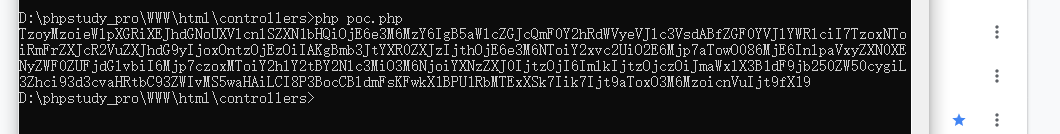
传进去:
一开始,传进去看到这个报错,以为没有成功,后来访问了一下1.php发现自己成功了QAQ
打开蚁剑,直接连上马:

看了一圈发现flag再根目录:
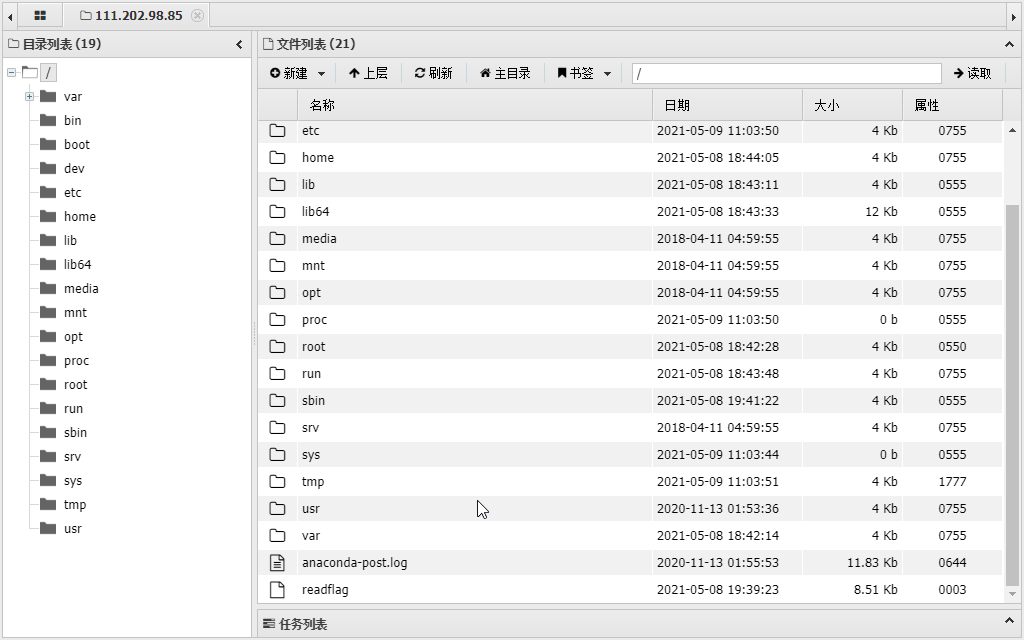
然后发现没有权限。。。。。。。又卡住了
但是我做题晚上刚刚复现了蓝帽的web题,有disable_functions绕过插件,就去试了一下

然后试着读了一下
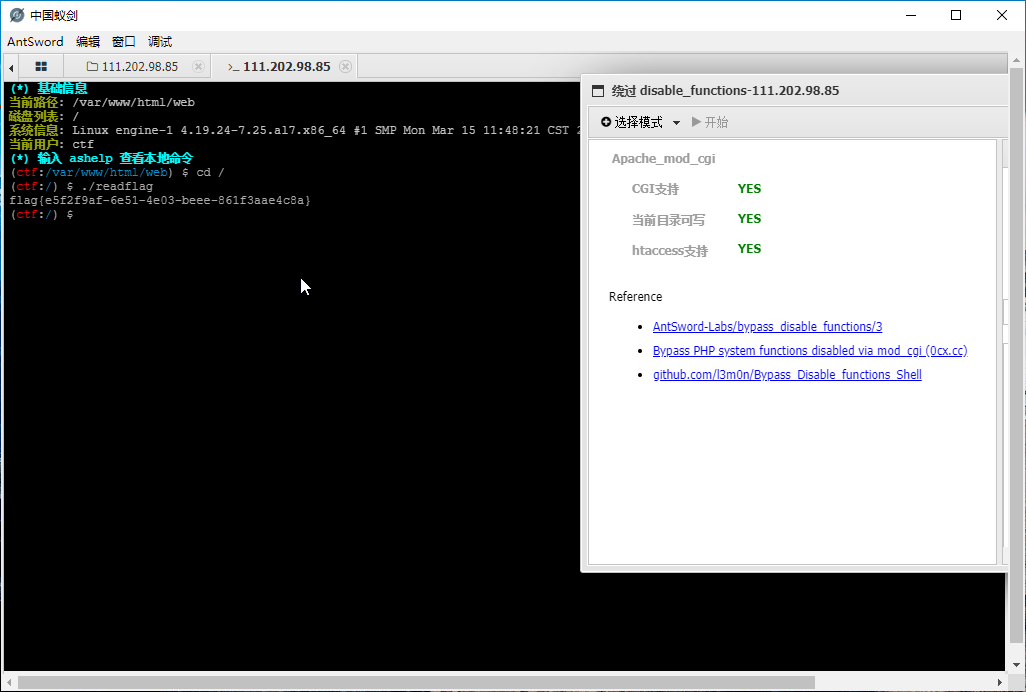
它就出来了!!!!!!!
是一道注入题
跑了一下sqlmap
发现了两个参数:
username password
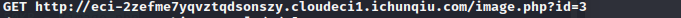
和/image.php下的id
注入了一下发现前两个都不是,随即对id下手
尝试了几种注入都无效,最后发现是异或注入
构造payload:
有回现,尝试变更参数
直到:
时没有回显,证明数据库第一位是c
获取第二位:
发现到117没有回显
证明第二位为t
依次类推,获得第三位为f
当数据库位数为4位时始终没有回显。证明只有三位,且数据库名为ctf
知道了数据库名就好办了,直接起脚本,依次爆):
获得表名为 users
之后依次修改url 继续 爆破
最终爆破出来密码为(当前环境下的密码):
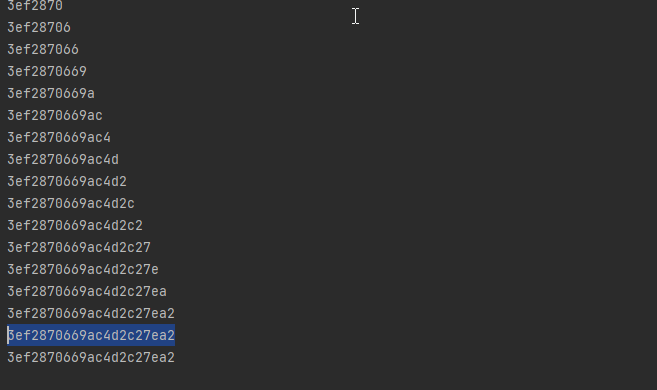
然后登录管理员账号:

抓包查看发现是ssrf 读取文件漏洞
构造payload:
获得flag

When I was a child,I also like to read Robots.txt
Here is what you want:1ndexx.php
When I was a child,I also like to read Robots.txt
Here is what you want:1ndexx.php
/.1ndexx.php.swp
<?php $link = mysql_connect('localhost', 'root'); ?>
<html>
<head>
<title>Hello worldd!</title>
<style>
body {
background-color: white;
text-align: center;
padding: 50px;
font-family: "Open Sans","Helvetica Neue",Helvetica,Arial,sans-serif;
}
margin-bottom: 40px;
}
</style>
</head>
<body>
<img id="logo" src="logo.png" />
<h1><?php echo "Hello My freind!"; ?></h1>
<?php if($link) { ?>
<h2>I Can't view my php files?!</h2>
<?php } else { ?>
<h2>MySQL Server version: <?php echo mysql_get_server_info(); ?></h2>
<?php } ?>
</body>
</html>
<?php
$file=fopen("flag.php","r") or die("Unable 2 open!");
$I_know_you_wanna_but_i_will_not_give_you_hhh = fread($file,filesize("flag.php"));
$hack=fopen("hack.php","w") or die("Unable 2 open");
$a=$_GET['code'];
if(preg_match('/system|eval|exec|base|compress|chr|ord|str|replace|pack|assert|preg|replace|create|function|call|\~|\^|\`|flag|cat|tac|more|tail|echo|require|include|proc|open|read|shell|file|put|get|contents|dir|link|dl|var|dump/',$a)){
die("you die");
}
if(strlen($a)>33){
die("nonono.");
}
fwrite($hack,$a);
fwrite($hack,$I_know_you_wanna_but_i_will_not_give_you_hhh);
fclose($file);
fclose($hack);
?>
<?php $link = mysql_connect('localhost', 'root'); ?>
<html>
<head>
<title>Hello worldd!</title>
<style>
body {
background-color: white;
text-align: center;
padding: 50px;
font-family: "Open Sans","Helvetica Neue",Helvetica,Arial,sans-serif;
}
margin-bottom: 40px;
}
</style>
</head>
<body>
<img id="logo" src="logo.png" />
<h1><?php echo "Hello My freind!"; ?></h1>
<?php if($link) { ?>
<h2>I Can't view my php files?!</h2>
<?php } else { ?>
<h2>MySQL Server version: <?php echo mysql_get_server_info(); ?></h2>
<?php } ?>
</body>
</html>
<?php
$file=fopen("flag.php","r") or die("Unable 2 open!");
$I_know_you_wanna_but_i_will_not_give_you_hhh = fread($file,filesize("flag.php"));
$hack=fopen("hack.php","w") or die("Unable 2 open");
$a=$_GET['code'];
if(preg_match('/system|eval|exec|base|compress|chr|ord|str|replace|pack|assert|preg|replace|create|function|call|\~|\^|\`|flag|cat|tac|more|tail|echo|require|include|proc|open|read|shell|file|put|get|contents|dir|link|dl|var|dump/',$a)){
die("you die");
}
if(strlen($a)>33){
die("nonono.");
}
fwrite($hack,$a);
fwrite($hack,$I_know_you_wanna_but_i_will_not_give_you_hhh);
fclose($file);
fclose($hack);
?>
/?code=<?php%20phpinfo();?>
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
最后于 2021-5-11 10:31
被H3h3QAQ编辑
,原因: