-
-
漏洞预警丨OpenSSH 远程代码执行漏洞(CVE-2024-6387)
-
发表于: 2024-7-2 13:40 3077
-
漏洞概述
OpenSSH是一个开源实现的SSH协议,用于加密网络通信。OpenSSH提供了一个安全的通道来访问远程计算机或服务器,并包含了一组客户端和服务器工具,以提供包括远程登录、远程执行命令、文件传输等功能。
CVE-2024-6387影响使用glibc的Linux系统,该漏洞被称为”RegreSSHion”。这个漏洞允许未经身份验证的用户在默认配置的情况下,通过LoginGraceTime参数进行远程代码执行,从而以root权限控制受影响的系统。
这个漏洞一旦被利用,可能会导致系统全面崩溃,攻击者可以使用最高权限执行任意代码,从而导致系统全面接管、安装恶意软件、篡改数据和创建后门进行持久访问。它可能会促进网络传播,使攻击者可以利用被入侵的系统作为立足点,穿越并利用组织内其他易受攻击的系统。
漏洞详情
目前该漏洞利用详情已公开,DayDayPoc平台收录了该漏洞poc,访问如下链接可查看漏洞poc
f41K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2V1k6s2m8G2j5#2)9J5k6h3y4G2L8g2)9J5c8V1c8h3b7W2)9J5k6o6t1H3x3U0c8Q4x3X3b7%4x3K6M7$3i4K6u0W2K9s2c8E0L8l9`.`.
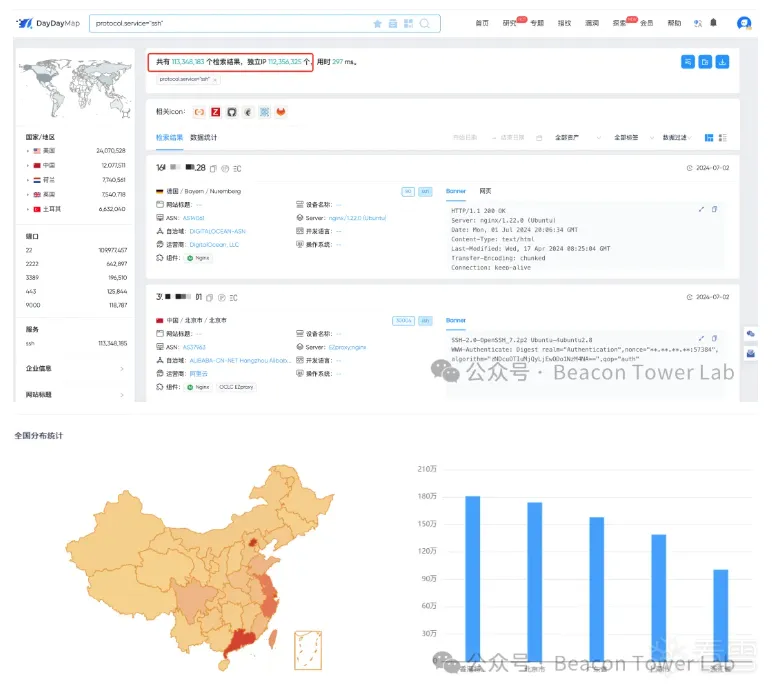
影响范围
根据DayDayMap(2cfN6%4N6%4i4K6u0W2k6r3q4&6k6r3q4&6L8h3q4H3i4K6u0W2j5$3!0E0i4K6t1&6i4@1f1#2i4K6R3#2i4@1p5^5i4@1f1%4i4K6V1H3i4K6R3K6i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1%4i4@1u0n7i4K6W2o6i4@1f1%4i4@1p5&6i4@1u0m8i4@1f1&6i4K6V1%4i4@1t1@1i4@1f1^5i4@1t1#2i4K6R3@1i4@1f1@1i4@1u0m8i4@1p5%4i4@1f1$3i4@1t1#2i4K6S2n7i4@1f1%4i4@1u0n7i4K6V1^5i4@1f1#2i4@1t1&6i4@1t1K6i4@1f1#2i4K6S2r3i4@1t1H3i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1$3i4K6V1#2i4@1t1H3i4@1f1$3i4K6S2p5i4@1q4q4i4@1f1$3i4K6V1^5i4@1u0q4i4@1f1%4i4@1p5@1i4@1u0m8i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4K6R3#2i4@1p5^5i4@1f1%4i4K6V1H3i4K6R3K6i4@1f1$3i4K6W2o6i4K6R3&6i4@1f1@1i4@1t1^5i4K6S2m8i4@1f1@1i4@1u0m8i4@1u0r3i4@1f1$3i4K6W2p5i4@1p5I4i4@1f1^5i4@1t1#2i4K6R3@1i4@1f1@1i4@1u0m8i4@1p5%4i4@1f1#2i4K6S2r3i4@1q4r3i4@1f1^5i4K6R3K6i4@1u0p5i4@1f1&6i4K6R3I4i4@1q4p5i4@1f1#2i4K6S2r3i4K6V1%4i4@1f1^5i4@1q4r3i4@1p5#2i4@1f1$3i4@1u0o6i4K6S2r3i4@1f1$3i4@1t1@1i4K6W2q4i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1#2i4@1u0p5i4@1t1I4i4@1f1#2i4K6V1K6i4K6S2p5i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1#2i4K6W2n7i4@1u0p5i4@1f1#2i4K6R3$3i4K6R3#2i4@1f1&6i4@1p5K6i4K6S2q4i4@1f1&6i4K6V1&6i4@1p5&6i4@1f1^5i4@1t1#2i4K6R3@1i4@1f1@1i4@1u0m8i4@1p5%4i4@1f1@1i4@1t1^5i4@1u0n7i4@1f1^5i4@1p5$3i4K6R3I4i4@1f1#2i4K6R3^5i4K6R3$3i4@1f1#2i4@1t1^5i4K6R3K6i4@1f1#2i4K6W2o6i4@1p5^5i4@1f1&6i4@1p5$3i4K6V1&6i4@1f1$3i4@1t1^5i4@1q4r3i4@1f1#2i4K6V1J5i4K6S2o6i4@1f1#2i4K6S2o6i4K6V1%4i4@1f1@1i4@1u0m8i4@1q4o6i4@1f1K6i4K6R3H3i4K6R3J5
DayDayMap查询语法:
protocol.service="ssh"
解决方案
目前官方已有可更新版本,建议受影响用户升级至最新版本:OpenSSH > 9.8p1
官方补丁下载地址:
Ubuntu 的软件源已更新:
196K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2I4N6h3q4D9P5i4y4Q4x3X3g2U0L8$3#2Q4x3V1j5J5x3o6t1@1i4K6u0r3x3o6N6Q4x3V1j5H3x3g2)9J5c8X3y4$3k6g2)9J5k6o6t1H3x3U0c8Q4x3X3b7$3x3K6R3%4i4K6u0r3M7X3g2Y4M7X3g2K6M7$3S2A6L8$3&6Q4x3X3g2@1P5s2b7`.
c35K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6#2j5Y4g2F1N6s2g2Q4x3X3g2U0L8$3#2Q4x3V1k6K6k6h3y4#2M7X3W2@1P5g2)9J5c8V1y4h3c8g2)9J5k6o6t1H3x3U0c8Q4x3X3b7$3x3K6R3%4
a97K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2G2M7r3g2F1M7%4y4Z5i4K6u0W2j5$3!0E0i4K6u0r3N6s2S2@1i4K6u0r3M7X3g2D9k6h3q4K6k6g2)9J5k6o6W2Q4x3X3f1^5
原文链接

