-
-
[原创] Clash Verge 1-Click RCE漏洞
-
发表于:
2025-5-20 21:04
1354
-
[原创] Clash Verge 1-Click RCE漏洞
用户使用默认配置的Clash Verge时,访问一个恶意网页即可触发本地文件写入攻击,进一步利用各种软件的插件加载机制,即可将文件写入扩展至RCE漏洞。本文以IDA的插件加载机制演示该例
名称
版本
地址
Clash Verge Rev
v2.2.4 alpha(当前最新)
e4cK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6U0L8r3q4K6K9q4)9J5k6s2k6W2M7X3N6W2i4K6u0V1M7X3g2$3i4K6u0r3j5$3I4S2M7$3S2Q4x3X3c8$3k6i4u0Y4k6g2)9J5k6s2u0W2N6R3`.`.
Mihomo
v1.19.8 (当前最新)
b3fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6y4k6i4c8S2b7%4g2T1k6g2S2Q4x3V1k6E0K9h3S2G2L8h3!0Q4x3V1k6@1M7X3g2W2i4K6u0r3e0h3g2@1j5b7`.`.
下图是Clash Verge的默认配置模版,它默认在127.0.0.1:9097开启API服务,且secret字段为空,不做鉴权。并且该API服务存在CORS问题,可被恶意网页利用
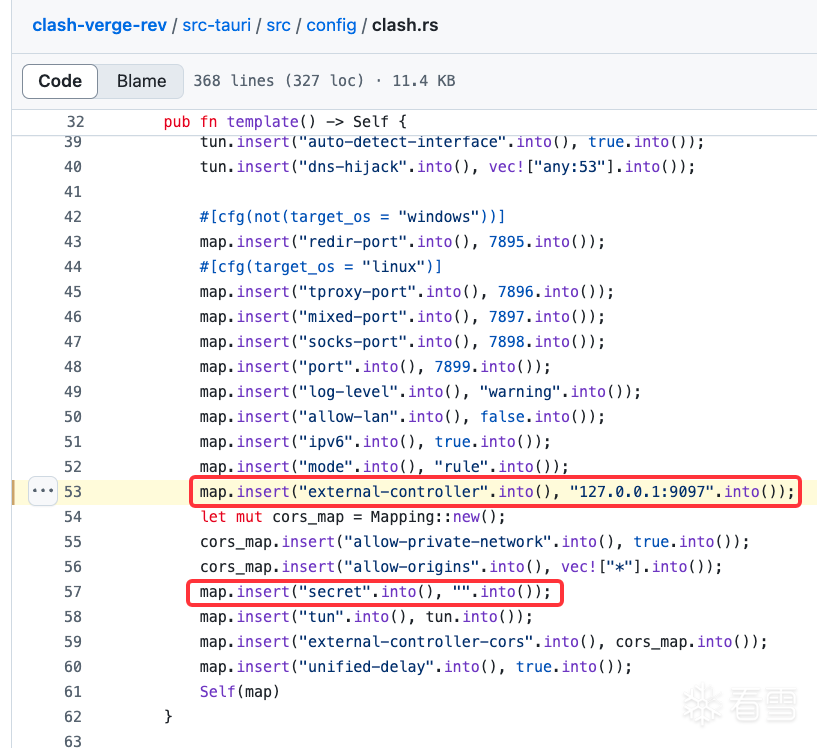
浏览Mihomo代码发现,通过PUT请求ee7K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5y4#2)9J5k6e0m8Q4x3X3f1H3i4K6u0W2x3g2)9K6b7e0V1H3z5e0N6Q4x3V1k6U0L8$3&6X3K9h3N6K6i4@1f1#2i4K6S2p5i4@1t1K6i4@1f1#2i4K6S2r3i4@1q4r3i4@1f1^5i4@1q4q4i4@1u0q4i4@1f1%4i4@1u0p5i4@1q4q4i4@1f1&6i4K6R3#2i4K6S2p5i4@1f1%4i4@1u0p5i4@1q4q4i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1g2r3i4@1u0o6i4K6S2o6b7X3!0V1P5g2!0q4y4q4!0n7z5q4!0n7b7f1A6e0e0@1&6Q4c8e0k6Q4b7e0m8Q4b7V1y4Q4c8e0g2Q4b7V1y4Q4z5p5k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5o6g2Q4b7U0k6Q4c8e0c8Q4b7U0S2Q4b7f1c8H3j5i4W2D9L8$3q4V1i4@1f1#2i4@1q4p5i4K6V1%4i4@1f1$3i4@1q4q4i4@1t1#2i4@1f1#2i4K6S2p5i4@1t1K6i4@1f1@1i4@1t1^5i4@1u0m8i4@1f1&6i4K6R3#2i4K6S2p5i4@1f1%4i4@1u0p5i4@1q4q4i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1#2i4K6R3$3i4K6R3#2i4@1f1#2i4@1q4q4i4@1t1&6
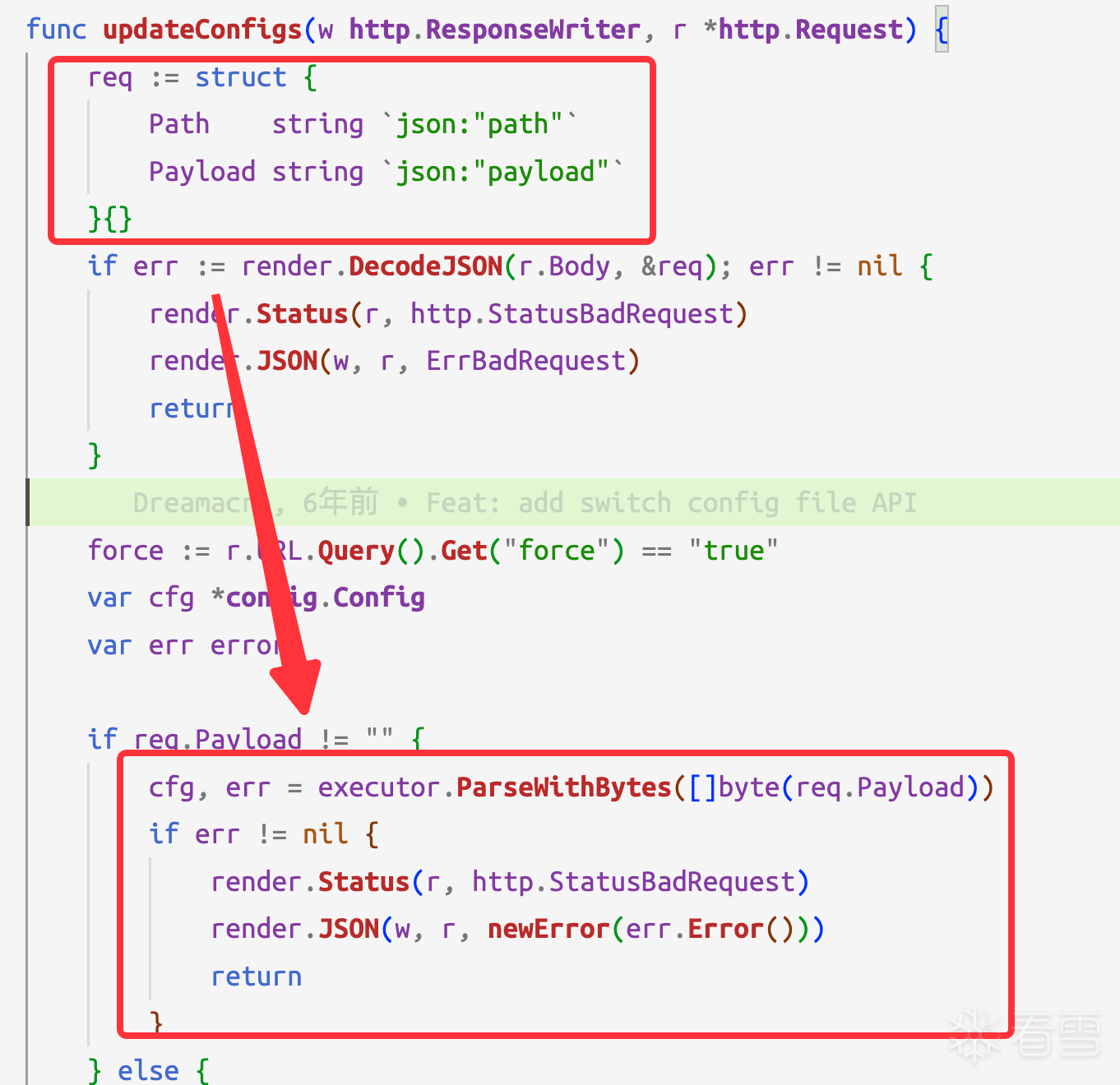
配置文件为YAML格式,并且其中的下载UI功能可被利用
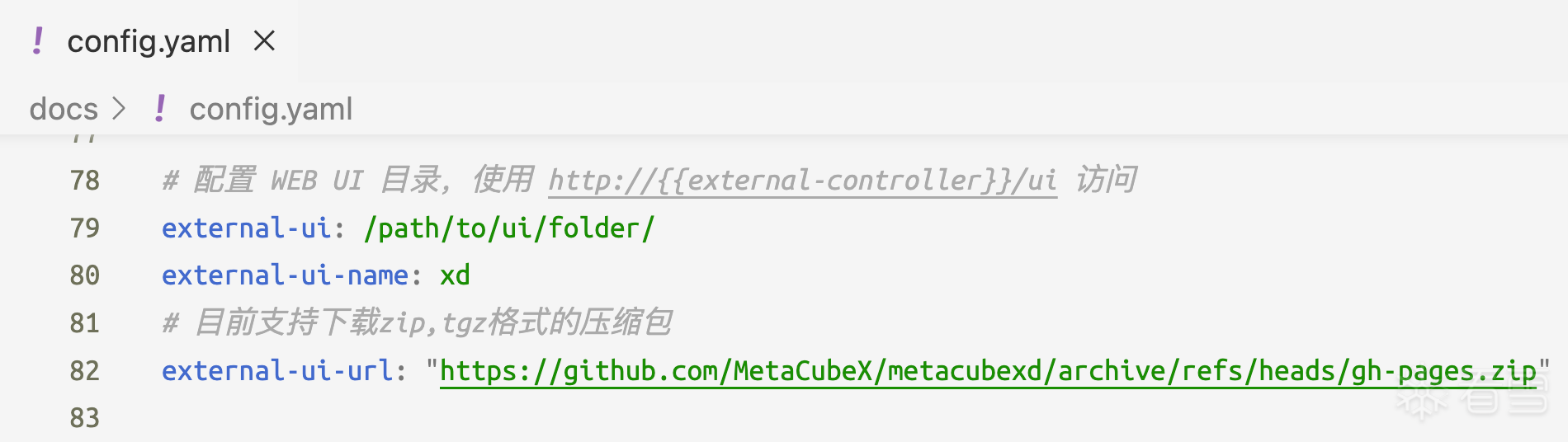
Mihomo对external-ui字段有路径检查,不管是相对路径还是绝对路径,都会解析然后检查是否仍然处于安全目录,如下图所示
[培训]科锐逆向工程师培训第53期2025年7月8日开班!