-
-
[原创]对Windows启动中bootmgfw.efi的分析
-
发表于: 2025-5-31 16:44 683
-
这篇文章会介绍Windows早期引导过程(bootmgfw.efi)
DebugService2是Windbg下提供最早附加到操作系统的时机,通过调用栈可以发现,其在DbgLoadImageSymbols被调用
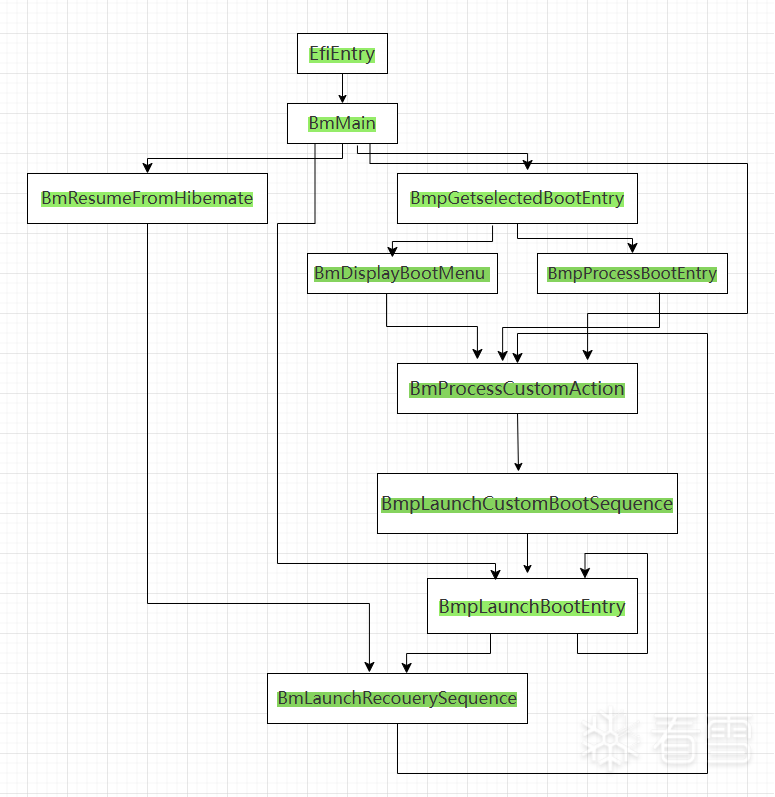
根据IDA的静态分析与调用栈分析,不难得出如下调用关系
那么,Windows又是如何知道应该call DebugService2呢?这便是BmMain的事了
BmMain做了什么
调用BmFwInitializeBootDirectoryPath用于初始化引导程序路径(\EFI\Microsoft\Boot)。
分析一下BmFwInitializeBootDirectoryPath
g_SbControl为全局变量,其0x8e0处为EFI_SYSTEN_TABLE的指针,HAL对其创建封装。
初始化引导程序路径后,调用BmOpenDataStore用于通过UEFI服务(磁盘I/O)挂载和读取BCD数据库文件(\EFI\Microsoft\Boot\BCD)。
此函数在 Windows 引导管理器启动过程中负责:获取 BCD (Boot Configuration Data) 存储路径,打开 BCD 存储以读取引导配置,为后续引导选项加载做准备。
这是恢复DebugService2的最初现场
在DebugSevice2被调用后,没有适合下断点的位置,所以直接下BmpLaunchBootEntry。
BmpLaunchBootEntry将加载并执行winload.efi。
BmpLaunchBootEntry函数之前的控制流根据之前提到的BCD存储的值选择正确的引导条目。如果启用了BitLocker,那么引导管理器在将控制转移到引导加载程序之前对系统分区进行解密。
图来自之前的帖子
分析一下BmpLaunchBootEntry
FvebpUnlockSinglePartition
这是BitLocker的解密函数,分析一下
设备处理流程:如果设备类型为5,使用系统默认控制设备,设备匹配时添加FLAG_200H标志。
针对VHD虚拟磁盘,先解锁宿主物理设备,递归调用时使用特殊标志FLAG_400H
核心解密函数:
BmFindAssociatedOsEntry,BmTransferExecution
这两个函数只是做了基本的参数转换,调用流程可以见下

BmpLaunchBootEntry函数接着执行BmpTransferExecution检查引导选项,ImgArchEfiStartBootApplication函数负责初始化winload.efi的受保护内存模式。在此之后,Archpx64TransferTo64BitApplicationAsm执行,该函数完成启动winload.efi的准备工作。
在这个关键点之后,所有的执行流都转移到winload.efi,它负责加载和初始化 Windows内核。在此之前,执行是在UEFI环境中通过引导服务进行的,并在flat内存下操作。
如果安全引导被禁用,恶意代码可以在引导过程的这个阶段对内存进行任何修改,因为内核模式模块还没有PatchGuard。PatchGuard只会在引导过程的后续步骤中进行初始化。
后面若有时间,会写对Winload的分析
请大家多指教
kd> lmstart end module name00000000`cf5f3000 00000000`cf7bd000 bootmgfw (pdb symbols) kd> k # Child-SP RetAddr Call Site00 00000000`cf570590 00000000`cf6c5023 bootmgfw!DbgLoadImageSymbols+0x6701 00000000`cf5705e0 00000000`cf6c551a bootmgfw!BlBdStart+0x19302 00000000`cf5706d0 00000000`cf66524d bootmgfw!BlBdInitialize+0x34203 00000000`cf5707b0 00000000`cf613ae7 bootmgfw!BlInitializeLibrary+0x9504 00000000`cf5707e0 00000000`cf61344d bootmgfw!BmMain+0x4eb05 00000000`cf570960 00000000`ce09283c bootmgfw!EfiEntry+0x1d06 00000000`cf570990 00000000`d40b9218 0xce09283c07 00000000`cf570998 00000000`d4da5918 0xd40b921808 00000000`cf5709a0 00000000`cf570a50 0xd4da591809 00000000`cf5709a8 00000000`00000000 0xcf570a50kd> lmstart end module name00000000`cf5f3000 00000000`cf7bd000 bootmgfw (pdb symbols) kd> k # Child-SP RetAddr Call Site00 00000000`cf570590 00000000`cf6c5023 bootmgfw!DbgLoadImageSymbols+0x6701 00000000`cf5705e0 00000000`cf6c551a bootmgfw!BlBdStart+0x19302 00000000`cf5706d0 00000000`cf66524d bootmgfw!BlBdInitialize+0x34203 00000000`cf5707b0 00000000`cf613ae7 bootmgfw!BlInitializeLibrary+0x9504 00000000`cf5707e0 00000000`cf61344d bootmgfw!BmMain+0x4eb05 00000000`cf570960 00000000`ce09283c bootmgfw!EfiEntry+0x1d06 00000000`cf570990 00000000`d40b9218 0xce09283c07 00000000`cf570998 00000000`d4da5918 0xd40b921808 00000000`cf5709a0 00000000`cf570a50 0xd4da591809 00000000`cf5709a8 00000000`00000000 0xcf570a50EfiEntry-->BmMain-->BlBdStart-->DebugService2EfiEntry-->BmMain-->BlBdStart-->DebugService2void BmFwInitializeBootDirectoryPath() { // 尝试打开引导设备 status = BlpDeviceOpen(g_SbControl+0x8e0, 1, NULL, &deviceHandle); if (!NT_SUCCESS(status)) { goto Cleanup; } // 获取应用程序目录路径 status = BmpFwGetApplicationDirectoryPath(&appDirPath, &appDirPathLen); if (!NT_SUCCESS(status) || !appDirPath) { goto Cleanup; } // 尝试打开目标文件 status = BlFileOpen(deviceHandle, tempBuffer, FILE_READ_DATA, &fileHandle); if (NT_SUCCESS(status)) { BootDirectory = appDirPath; appDirPath = NULL; }Cleanup: //这里关闭HANDLE // 失败时设置默认路径\\EFI\\Boot\\bootmgfw.efi if (!BootDirectory) { BootDirectory = (WCHAR*)DEFAULT_BOOT_DIR; }}void BmFwInitializeBootDirectoryPath() { // 尝试打开引导设备 status = BlpDeviceOpen(g_SbControl+0x8e0, 1, NULL, &deviceHandle); if (!NT_SUCCESS(status)) { goto Cleanup; } // 获取应用程序目录路径 status = BmpFwGetApplicationDirectoryPath(&appDirPath, &appDirPathLen); if (!NT_SUCCESS(status) || !appDirPath) { goto Cleanup; } // 尝试打开目标文件 status = BlFileOpen(deviceHandle, tempBuffer, FILE_READ_DATA, &fileHandle); if (NT_SUCCESS(status)) { BootDirectory = appDirPath; appDirPath = NULL; }Cleanup: //这里关闭HANDLE // 失败时设置默认路径\\EFI\\Boot\\bootmgfw.efi if (!BootDirectory) { BootDirectory = (WCHAR*)DEFAULT_BOOT_DIR; }}NTSTATUS BmOpenDataStore(PVOID Context) { part1=NULL; part2=NULL; // 获取数据存储路径 status = BmGetDataStorePath(&part1, &part2, &freePart2); if (!NT_SUCCESS(status)) { goto Cleanup; } // 计算 part2 字符串长度(不包括空终止符) for (part2Length = 0; part2[part2Length] != L'\0'; part2Length++); // 计算组合路径所需的总字节数 ULONG totalBytes = (part2Length + 1) * sizeof(WCHAR); // 包含空终止符 if (part1->LengthField > (ULONG_MAX - totalBytes)) { status = STATUS_INTEGER_OVERFLOW; goto Cleanup; } totalBytes += part1->LengthField; // 检查是否超过最大限制(0xFFFFFFFF) if (totalBytes > 0xFFFFFFFF) { status = STATUS_INTEGER_OVERFLOW; goto Cleanup; } // 分配内存 combinedPath = BlMmAllocateHeap(totalBytes); if (!combinedPath) { status = STATUS_INSUFFICIENT_RESOURCES; goto Cleanup; } // 复制 part1 数据 memcpy(combinedPath, part1->Buffer, part1->LengthField); // 复制 part2 数据(包括空终止符) memcpy((PBYTE)combinedPath + part1->LengthField, part2, (part2Length + 1) * sizeof(WCHAR)); // 设置 UNICODE_STRING 结构,即fullPath // 打开 BCD 存储 status = BcdOpenStoreFromFile(&fullPath, Context);Cleanup: // 释放资源 if (combinedPath) { BlMmFreeHeap(combinedPath); } if (part1) { BlMmFreeHeap(part1); } if (part2 && freePart2) { BlMmFreeHeap(part2); } return status;}NTSTATUS BmOpenDataStore(PVOID Context) { part1=NULL; part2=NULL; // 获取数据存储路径 status = BmGetDataStorePath(&part1, &part2, &freePart2); if (!NT_SUCCESS(status)) { goto Cleanup; } // 计算 part2 字符串长度(不包括空终止符) for (part2Length = 0; part2[part2Length] != L'\0'; part2Length++); // 计算组合路径所需的总字节数 ULONG totalBytes = (part2Length + 1) * sizeof(WCHAR); // 包含空终止符 if (part1->LengthField > (ULONG_MAX - totalBytes)) { status = STATUS_INTEGER_OVERFLOW; goto Cleanup; } totalBytes += part1->LengthField; // 检查是否超过最大限制(0xFFFFFFFF) if (totalBytes > 0xFFFFFFFF) { status = STATUS_INTEGER_OVERFLOW; goto Cleanup; } // 分配内存 combinedPath = BlMmAllocateHeap(totalBytes); if (!combinedPath) { status = STATUS_INSUFFICIENT_RESOURCES; goto Cleanup; } // 复制 part1 数据 memcpy(combinedPath, part1->Buffer, part1->LengthField); // 复制 part2 数据(包括空终止符) memcpy((PBYTE)combinedPath + part1->LengthField, part2, (part2Length + 1) * sizeof(WCHAR)); // 设置 UNICODE_STRING 结构,即fullPath // 打开 BCD 存储 status = BcdOpenStoreFromFile(&fullPath, Context);Cleanup: // 释放资源 if (combinedPath) { BlMmFreeHeap(combinedPath); } if (part1) { BlMmFreeHeap(part1); } if (part2 && freePart2) { BlMmFreeHeap(part2); } return status;}cf70b9c4 488bc4 mov rax, rspcf70b9c7 4c894018 mov qword ptr [rax+18h], r8cf70b9cb 53 push rbxcf70b9cc 4883ec40 sub rsp, 40hcf70b9d0 488348e0ff or qword ptr [rax-20h], 0FFFFFFFFFFFFFFFFhcf70b9d5 4c8d4818 lea r9, [rax+18h]cf70b9d9 4883601800 and qword ptr [rax+18h], 0cf70b9de 4533c0 xor r8d, r8dcf70b9e1 488bd9 mov rbx, rcxcf70b9e4 488950d8 mov qword ptr [rax-28h], rdxcf70b9e8 418d4801 lea ecx, [r8+1]cf70b9ec e883f6f3ff call bootmgfw!RtlImageNtHeaderEx (cf64b074)cf70b9f1 488b542460 mov rdx, qword ptr [rsp+60h]cf70b9f6 4885d2 test rdx, rdxcf70b9f9 7410 je bootmgfw!DbgLoadImageSymbols+0x47 (cf70ba0b)cf70b9fb 8b4258 mov eax, dword ptr [rdx+58h]cf70b9fe 89442430 mov dword ptr [rsp+30h], eaxcf70ba02 8b4250 mov eax, dword ptr [rdx+50h]cf70ba05 89442434 mov dword ptr [rsp+34h], eaxcf70ba09 eb0d jmp bootmgfw!DbgLoadImageSymbols+0x54 (cf70ba18)cf70ba0b 8364243000 and dword ptr [rsp+30h], 0cf70ba10 c744243400001000 mov dword ptr [rsp+34h], 100000hcf70ba18 41b803000000 mov r8d, 3cf70ba1e 488d542420 lea rdx, [rsp+20h]cf70ba23 488bcb mov rcx, rbxcf70ba26 e8e5c80300 call bootmgfw!DebugService2 (cf748310)cf70ba2b 4883c440 add rsp, 40h :在这里恢复cf70ba2f 5b pop rbxcf70ba30 c3 ret cf70b9c4 488bc4 mov rax, rspcf70b9c7 4c894018 mov qword ptr [rax+18h], r8cf70b9cb 53 push rbxcf70b9cc 4883ec40 sub rsp, 40hcf70b9d0 488348e0ff or qword ptr [rax-20h], 0FFFFFFFFFFFFFFFFhcf70b9d5 4c8d4818 lea r9, [rax+18h]cf70b9d9 4883601800 and qword ptr [rax+18h], 0cf70b9de 4533c0 xor r8d, r8dcf70b9e1 488bd9 mov rbx, rcxcf70b9e4 488950d8 mov qword ptr [rax-28h], rdxcf70b9e8 418d4801 lea ecx, [r8+1]cf70b9ec e883f6f3ff call bootmgfw!RtlImageNtHeaderEx (cf64b074)cf70b9f1 488b542460 mov rdx, qword ptr [rsp+60h]cf70b9f6 4885d2 test rdx, rdxcf70b9f9 7410 je bootmgfw!DbgLoadImageSymbols+0x47 (cf70ba0b)cf70b9fb 8b4258 mov eax, dword ptr [rdx+58h]cf70b9fe 89442430 mov dword ptr [rsp+30h], eaxcf70ba02 8b4250 mov eax, dword ptr [rdx+50h]cf70ba05 89442434 mov dword ptr [rsp+34h], eaxcf70ba09 eb0d jmp bootmgfw!DbgLoadImageSymbols+0x54 (cf70ba18)cf70ba0b 8364243000 and dword ptr [rsp+30h], 0cf70ba10 c744243400001000 mov dword ptr [rsp+34h], 100000hcf70ba18 41b803000000 mov r8d, 3cf70ba1e 488d542420 lea rdx, [rsp+20h]cf70ba23 488bcb mov rcx, rbxcf70ba26 e8e5c80300 call bootmgfw!DebugService2 (cf748310)cf70ba2b 4883c440 add rsp, 40h :在这里恢复cf70ba2f 5b pop rbxcf70ba30 c3 ret bootmgfw!BmpLaunchBootEntry (00000000`cf6150f4) bootmgfw!BmpLaunchBootEntry+0x49 (00000000`cf61513d): call to bootmgfw!BcdUtilGetBootOption (00000000`cf6a2794) bootmgfw!BmpLaunchBootEntry+0x5b (00000000`cf61514f): call to bootmgfw!BmOpenDataStore (00000000`cf617dc0) bootmgfw!BmpLaunchBootEntry+0x78 (00000000`cf61516c): call to bootmgfw!BmPurgeOption (00000000`cf618334) bootmgfw!BmpLaunchBootEntry+0x81 (00000000`cf615175): call to bootmgfw!BmCloseDataStore (00000000`cf617ed8) bootmgfw!BmpLaunchBootEntry+0x8c (00000000`cf615180): call to bootmgfw!BcdUtilGetBootOption (00000000`cf6a2794) bootmgfw!BmpLaunchBootEntry+0x9e (00000000`cf615192): call to bootmgfw!BmOpenDataStore (00000000`cf617dc0) bootmgfw!BmpLaunchBootEntry+0xbb (00000000`cf6151af): call to bootmgfw!BmPurgeOption (00000000`cf618334) bootmgfw!BmpLaunchBootEntry+0xc4 (00000000`cf6151b8): call to bootmgfw!BmCloseDataStore (00000000`cf617ed8) bootmgfw!BmpLaunchBootEntry+0x10c (00000000`cf615200): call to bootmgfw!BlGetBootOptionDevice (00000000`cf6658c0) bootmgfw!BmpLaunchBootEntry+0x135 (00000000`cf615229): call to bootmgfw!BlGetBootOptionBoolean (00000000`cf6654d0) bootmgfw!BmpLaunchBootEntry+0x15a (00000000`cf61524e): call to bootmgfw!BmFindAssociatedOsEntry (00000000`cf618ad4) bootmgfw!BmpLaunchBootEntry+0x17a (00000000`cf61526e): call to bootmgfw!BlGetBootOptionDevice (00000000`cf6658c0) bootmgfw!BmpLaunchBootEntry+0x19e (00000000`cf615292): call to bootmgfw!BlMmFreeHeap (00000000`cf68bd48) bootmgfw!BmpLaunchBootEntry+0x1ab (00000000`cf61529f): call to bootmgfw!BlMmFreeHeap (00000000`cf68bd48) bootmgfw!BmpLaunchBootEntry+0x1cf (00000000`cf6152c3): call to bootmgfw!BlMmFreeHeap (00000000`cf68bd48) bootmgfw!BmpLaunchBootEntry+0x1d7 (00000000`cf6152cb): call to bootmgfw!BmpCreateDevices (00000000`cf615e6c) bootmgfw!BmpLaunchBootEntry+0x1f7 (00000000`cf6152eb): call to bootmgfw!McTemplateK0qq_McGenEventWriteBoot (00000000`cf61350c) bootmgfw!BmpLaunchBootEntry+0x205 (00000000`cf6152f9): call to bootmgfw!BlFveRegisterBootEntryForTrustedWimBoot (00000000`cf62b9e8) bootmgfw!BmpLaunchBootEntry+0x243 (00000000`cf615337): call to bootmgfw!FvebpUnlockSinglePartition (00000000`cf62be60) bootmgfw!BmpLaunchBootEntry+0x255 (00000000`cf615349): call to bootmgfw!BlFveRegisterDeviceForTrustedWimBoot (00000000`cf62b964) bootmgfw!BmpLaunchBootEntry+0x274 (00000000`cf615368): call to bootmgfw!FvebpLogError (00000000`cf62bb28) bootmgfw!BmpLaunchBootEntry+0x2a1 (00000000`cf615395): call to bootmgfw!BlGetBootOptionBoolean (00000000`cf6654d0) bootmgfw!BmpLaunchBootEntry+0x2b8 (00000000`cf6153ac): call to bootmgfw!BlAppendBootOptionBoolean (00000000`cf665e2c) bootmgfw!BmpLaunchBootEntry+0x2c3 (00000000`cf6153b7): call to bootmgfw!BlRemoveBootOption (00000000`cf666128) bootmgfw!BmpLaunchBootEntry+0x2ce (00000000`cf6153c2): call to bootmgfw!BlRemoveBootOption (00000000`cf666128) bootmgfw!BmpLaunchBootEntry+0x2e2 (00000000`cf6153d6): call to bootmgfw!BlGetBootOptionBoolean (00000000`cf6654d0) bootmgfw!BmpLaunchBootEntry+0x2f9 (00000000`cf6153ed): call to bootmgfw!BlAppendBootOptionBoolean (00000000`cf665e2c) bootmgfw!BmpLaunchBootEntry+0x304 (00000000`cf6153f8): call to bootmgfw!BlRemoveBootOption (00000000`cf666128) bootmgfw!BmpLaunchBootEntry+0x30f (00000000`cf615403): call to bootmgfw!BlRemoveBootOption (00000000`cf666128) bootmgfw!BmpLaunchBootEntry+0x31f (00000000`cf615413): call to bootmgfw!BmTransferExecution (00000000`cf61457c) bootmgfw!BmpLaunchBootEntry+0x32f (00000000`cf615423): call to bootmgfw!BlFveRegisterBootEntryForTrustedWimBoot (00000000`cf62b9e8) bootmgfw!BmpLaunchBootEntry+0x383 (00000000`cf615477): call to bootmgfw!BcdUtilGetBootOption (00000000`cf6a2794) bootmgfw!BmpLaunchBootEntry+0x3be (00000000`cf6154b2): call to bootmgfw!BlGetBootOptionBoolean (00000000`cf6654d0) bootmgfw!BmpLaunchBootEntry+0x3ea (00000000`cf6154de): call to bootmgfw!BlGetBootOptionBoolean (00000000`cf6654d0) bootmgfw!BmpLaunchBootEntry+0x417 (00000000`cf61550b): call to bootmgfw!BlFveRegisterBootEntryForTrustedWimBoot (00000000`cf62b9e8) bootmgfw!BmpLaunchBootEntry+0x421 (00000000`cf615515): call to bootmgfw!BmLaunchRecoverySequence (00000000`cf6143ac) bootmgfw!BmpLaunchBootEntry+0x436 (00000000`cf61552a): call to bootmgfw!BlFveRegisterBootEntryForTrustedWimBoot (00000000`cf62b9e8) bootmgfw!BmpLaunchBootEntry+0x451 (00000000`cf615545): call to bootmgfw!BlRemoveBootOption (00000000`cf666128) bootmgfw!BmpLaunchBootEntry+0x474 (00000000`cf615568): call to bootmgfw!BmFatalErrorEx (00000000`cf61a020) bootmgfw!BmpLaunchBootEntry+0x479 (00000000`cf61556d): call to bootmgfw!BmpPreserveBootmgrLogToBootstat (00000000`cf615998) bootmgfw!BmpLaunchBootEntry+0x483 (00000000`cf615577): call to bootmgfw!BmDisplayDumpError (00000000`cf616870) bootmgfw!BmpLaunchBootEntry+0x48b (00000000`cf61557f): call to bootmgfw!BmErrorPurge (00000000`cf61a5a4) bootmgfw!BmpLaunchBootEntry+0x4e2 (00000000`cf6155d6): call to bootmgfw!BlAppendBootOptionBoolean (00000000`cf665e2c) bootmgfw!BmpLaunchBootEntry+0x514 (00000000`cf615608): call to bootmgfw!BmOpenDataStore (00000000`cf617dc0) bootmgfw!BmpLaunchBootEntry+0x526 (00000000`cf61561a): call to bootmgfw!BmProcessCustomAction (00000000`cf614538) bootmgfw!BmpLaunchBootEntry+0x535 (00000000`cf615629): call to bootmgfw!BmCloseDataStore (00000000`cf617ed8)bootmgfw!BmpLaunchBootEntry (00000000`cf6150f4) bootmgfw!BmpLaunchBootEntry+0x49 (00000000`cf61513d): call to bootmgfw!BcdUtilGetBootOption (00000000`cf6a2794) bootmgfw!BmpLaunchBootEntry+0x5b (00000000`cf61514f): call to bootmgfw!BmOpenDataStore (00000000`cf617dc0) bootmgfw!BmpLaunchBootEntry+0x78 (00000000`cf61516c): call to bootmgfw!BmPurgeOption (00000000`cf618334) bootmgfw!BmpLaunchBootEntry+0x81 (00000000`cf615175): call to bootmgfw!BmCloseDataStore (00000000`cf617ed8) bootmgfw!BmpLaunchBootEntry+0x8c (00000000`cf615180): call to bootmgfw!BcdUtilGetBootOption (00000000`cf6a2794) bootmgfw!BmpLaunchBootEntry+0x9e (00000000`cf615192): call to bootmgfw!BmOpenDataStore (00000000`cf617dc0) bootmgfw!BmpLaunchBootEntry+0xbb (00000000`cf6151af): call to bootmgfw!BmPurgeOption (00000000`cf618334) bootmgfw!BmpLaunchBootEntry+0xc4 (00000000`cf6151b8): call to bootmgfw!BmCloseDataStore (00000000`cf617ed8) bootmgfw!BmpLaunchBootEntry+0x10c (00000000`cf615200): call to bootmgfw!BlGetBootOptionDevice (00000000`cf6658c0) bootmgfw!BmpLaunchBootEntry+0x135 (00000000`cf615229): call to bootmgfw!BlGetBootOptionBoolean (00000000`cf6654d0) bootmgfw!BmpLaunchBootEntry+0x15a (00000000`cf61524e): call to bootmgfw!BmFindAssociatedOsEntry (00000000`cf618ad4) bootmgfw!BmpLaunchBootEntry+0x17a (00000000`cf61526e): call to bootmgfw!BlGetBootOptionDevice (00000000`cf6658c0) bootmgfw!BmpLaunchBootEntry+0x19e (00000000`cf615292): call to bootmgfw!BlMmFreeHeap (00000000`cf68bd48) bootmgfw!BmpLaunchBootEntry+0x1ab (00000000`cf61529f): call to bootmgfw!BlMmFreeHeap (00000000`cf68bd48) bootmgfw!BmpLaunchBootEntry+0x1cf (00000000`cf6152c3): call to bootmgfw!BlMmFreeHeap (00000000`cf68bd48) bootmgfw!BmpLaunchBootEntry+0x1d7 (00000000`cf6152cb): call to bootmgfw!BmpCreateDevices (00000000`cf615e6c) bootmgfw!BmpLaunchBootEntry+0x1f7 (00000000`cf6152eb): call to bootmgfw!McTemplateK0qq_McGenEventWriteBoot (00000000`cf61350c) bootmgfw!BmpLaunchBootEntry+0x205 (00000000`cf6152f9): call to bootmgfw!BlFveRegisterBootEntryForTrustedWimBoot (00000000`cf62b9e8) bootmgfw!BmpLaunchBootEntry+0x243 (00000000`cf615337): call to bootmgfw!FvebpUnlockSinglePartition (00000000`cf62be60) bootmgfw!BmpLaunchBootEntry+0x255 (00000000`cf615349): call to bootmgfw!BlFveRegisterDeviceForTrustedWimBoot (00000000`cf62b964) bootmgfw!BmpLaunchBootEntry+0x274 (00000000`cf615368): call to bootmgfw!FvebpLogError (00000000`cf62bb28) bootmgfw!BmpLaunchBootEntry+0x2a1 (00000000`cf615395): call to bootmgfw!BlGetBootOptionBoolean (00000000`cf6654d0) bootmgfw!BmpLaunchBootEntry+0x2b8 (00000000`cf6153ac): call to bootmgfw!BlAppendBootOptionBoolean (00000000`cf665e2c) bootmgfw!BmpLaunchBootEntry+0x2c3 (00000000`cf6153b7): call to bootmgfw!BlRemoveBootOption (00000000`cf666128) bootmgfw!BmpLaunchBootEntry+0x2ce (00000000`cf6153c2):
