-
-
[原创]漏洞预警 | VMware ESXi 存在缓冲区溢出漏洞(CVE-2025-22224)
-
发表于: 2025-3-6 18:20 1850
-
近日,Broadcom 发布VMware ESXi存在三个严重漏洞(CVE-2025-22224、CVE-2025-22225、CVE-2025-22226)并得到Vmware确认。为避免您的业务受影响,建议您及时开展安全风险自查。
VMware ESXi是VMware开发的企业级虚拟机监控程序,用于硬件虚拟化。,ESXi不是安装在操作系统上的软件应用程序,而是直接安装在硬件上并且集成了重要的操作系统组件。VMware ESXi原名ESX,2010年ESX4.1版本发布后,VMware将ESX更名为ESXi。ESXi被广泛应用于数据中心、云架构平台等。
据描述,由于 VMware ESXi 的虚拟机通信接口存在条件竞争,导致存在缓冲区溢出漏洞,攻击者可以利用此漏洞操控任意内存读写,窃取内存中敏感数据、从虚拟机中突破限制控制 VMware ESXi 宿主机,威胁整个服务器安全。
漏洞影响的产品和版本:
VMware ESXi 8.0 未打 ESXi80U3d-24585383补丁
VMware ESXi 7.0 未打 ESXi70U3s-24585291补丁
以下产品也受该漏洞影响:
VMware Workstation 17.x < 17.6.3
VMware Fusion 13.x< 13.6.3
VMware Cloud Foundation 4.5.x, 5.x 未打 ESXi80U3d-24585383补丁
VMware Telco Cloud Platform 3.x, 2.x 未打 KB389385 补丁
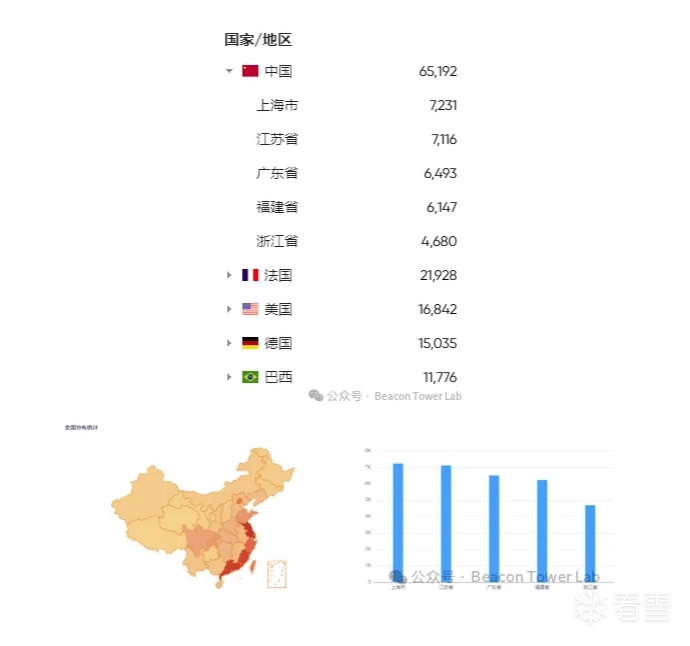
资产测绘
据daydaymap数据显示互联网存在226,385个资产,国内风险资产分布情况如下,主要分布在国内沿海省份。
解决方案
1、临时缓解方案
① 限制网络访,配置ip白名单,限制指定来源IP访问;
② 部署针对 VMware ESXi 平台安全监控系统,确保及时检测响应异常行为。
2、升级修复方案,官方已发布漏洞修复补丁
ESXi 8.0 请更新至
① 8.0 Update 3d(build 24585383),补丁地址:
② 8.0 Update 2d(build 24585300),补丁地址:
ESXi 7.0 请更新至
7.0 Update 3s(build 24585291),补丁地址:
参考链接

