-
-
[原创]漏洞预警 | Windows 文件资源管理器欺骗漏洞(CVE-2025-24071、CVE-2025-24054)
-
发表于: 2025-3-31 11:02 1142
-
1漏洞概述
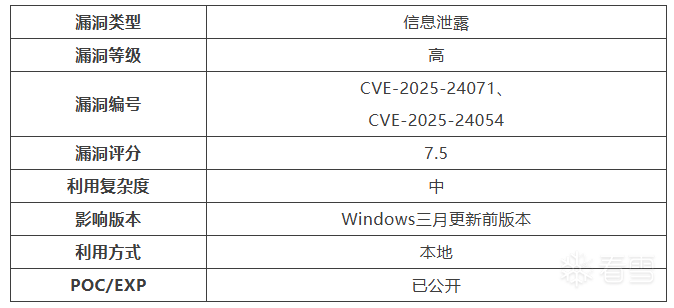
近日,微软发布windows操作系统更新修复漏洞,其中Windows 文件资源管理器欺骗漏洞(CVE-2025-24071、CVE-2025-24054)正被广泛利用,建议您及时开展安全风险自查。
据描述,由于windows的资源管理器默认信任libray-ms文件,支持读取此类文件进行渲染图标、缩略图和详细信息。当压缩包内存在此类文件时,用户解压包含smb(文件共享服务)路径配置的libray-ms文件,会自动被windows资源管理器内置文件解析机制解析,将受害者的NTLM身份信息发送到攻击者smb服务器。攻击者利用这种隐式信任和自动文件处理行为来泄露凭据,然后可以利用这些凭据进行哈希传递攻击或脱机 NTLM 哈希破解。攻击者可以利用该漏洞以管理员权限执行操作,包括但不限于创建新用户、修改现有用户的权限、安装恶意软件等。
漏洞影响的产品和版本:
Windows Server 2022
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1607 for 32-bit Systems
Windows 10 for x64-based Systems
Windows 10 for 32-bit Systems
Windows Server 2025
Windows 11 Version 24H2 for x64-based Systems
Windows 11 Version 24H2 for ARM64-based Systems
Windows Server 2022, 23H2 Edition (Server Core installation)
Windows 11 Version 23H2 for x64-based Systems
Windows 11 Version 23H2 for ARM64-based Systems
Windows Server 2025 (Server Core installation)
Windows 10 Version 22H2 for 32-bit Systems
Windows 10 Version 22H2 for ARM64-based Systems
Windows 10 Version 22H2 for x64-based Systems
Windows 11 Version 22H2 for x64-based Systems
Windows 11 Version 22H2 for ARM64-based Systems
Windows 10 Version 21H2 for x64-based Systems
Windows 10 Version 21H2 for ARM64-based Systems
Windows 10 Version 21H2 for 32-bit Systems
Windows Server 2022 (Server Core installation)
2漏洞复现

3资产测绘
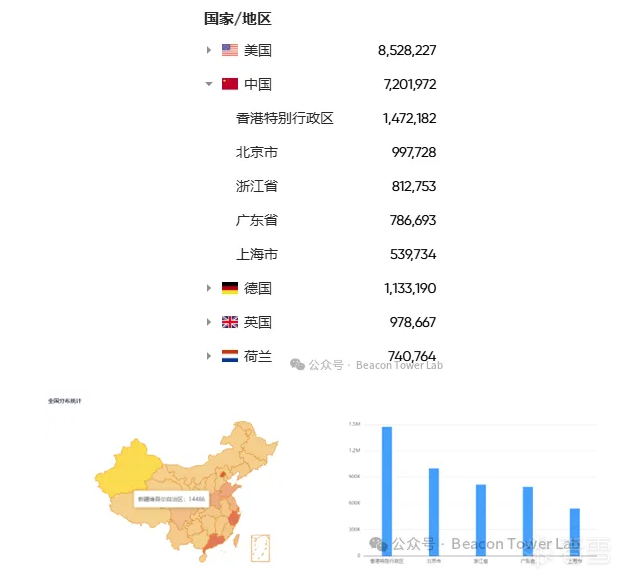
据daydaymap数据显示互联网存在29,294,851个资产,国内风险资产分布情况如下:
4解决方案
升级修复
目前windows已发布修复安全补丁:
5参考链接
dfaK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0M7%4u0U0i4K6u0W2L8h3W2U0M7X3!0K6L8$3k6@1i4K6u0W2j5$3!0E0i4K6u0r3N6i4m8V1j5i4c8W2i4K6u0V1k6%4g2A6k6r3g2Q4x3V1k6$3N6h3I4F1k6i4u0S2j5X3W2D9K9i4c8&6i4K6u0r3b7#2k6q4i4K6u0V1x3U0l9J5y4g2)9J5k6o6t1@1x3o6f1@1
cfaK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2V1k6s2m8G2j5#2)9J5k6h3y4G2L8g2)9J5c8V1c8h3b7W2)9J5k6o6t1H3x3U0y4Q4x3X3b7^5z5e0V1&6i4K6u0W2K9s2c8E0L8l9`.`.
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

